DNS በHTTPS ምንድነው? ወደ የተደገፈ መረጃ መምሪያ
DNS በHTTPS (DoH) ምንድነው የሚለው ምንድን ነው? ይህ መመሪያ የDoH የDNS ፍለጋዎችዎን እንዴት ይደበቃል እና የግል ዕይታ ለማሻሻል፣ እንዲያወጣ ይረዳል፣ እና የእርስዎን ጉብኝት ይደረግ ይሆን ይገልጻል።

የተመነጨ ማስተካከያዎች
DNS over HTTPS, or DoH, is a modern protocol designed to keep your web browsing private. It does this by encrypting the very first step you take online: looking up a website's address. Think of it like swapping a public postcard for a sealed, private letter. Your request is hidden from prying eyes on the network.
The Privacy Problem DNS Over HTTPS Solves
Whenever you visit a website, your device needs to translate the human-friendly name you type (like example.com) into a machine-readable IP address. This is handled by the Domain Name System (DNS), which is essentially the internet's phonebook.
For decades, this DNS lookup has been completely unencrypted, happening out in the open. That means your Internet Service Provider (ISP), your office network administrator, or anyone snooping on a public Wi-Fi connection can see every single site you look up. It’s like announcing your destination to everyone in the room before you go there.
This lack of privacy creates some serious issues:
- ISP Tracking: Your internet provider can easily log your entire browsing history. They can use this data for targeted advertising or sell it to data brokers.
- Eavesdropping on Public Wi-Fi: On a coffee shop or airport network, attackers can easily watch your DNS requests to profile you or see what services you use.
- DNS Hijacking: A bad actor could intercept your unencrypted DNS request and send back a fake IP address, redirecting you to a phishing site designed to steal your credentials.
Sealing the Digital Envelope
DNS over HTTPS changes the game by wrapping these DNS lookups inside the same secure HTTPS protocol that protects your online banking and shopping. This innovation, pushed forward by major players like Google and Mozilla starting around 2016, makes your DNS requests look just like any other encrypted web traffic.
This diagram shows how DoH neatly tucks the DNS query inside a secure HTTPS tunnel, sending it safely to the resolver.
The crucial part is that both your request and the server's response are shielded inside this encrypted connection. No one in the middle can see or tamper with them. You can find more historical context on the origins of DoH from Control D.
By blending DNS requests with normal HTTPS traffic, DoH effectively camouflages your browsing intentions, making it incredibly difficult for third parties to track your online journey from the very first step.
This simple but powerful change adds a much-needed layer of privacy that was missing from the internet's original design.
Traditional DNS vs DNS over HTTPS at a Glance
To really see the difference, let's put the old and new methods side-by-side. The contrast in privacy and security is stark.
| Feature | Traditional DNS | DNS over HTTPS (DoH) |
|---|---|---|
| Encryption | None. Sent in plain text. | Fully encrypted with HTTPS. |
| Port | Uses port 53. | Uses port 443 (standard for HTTPS). |
| Visibility | Easily monitored by ISPs and networks. | Blends in with normal web traffic. |
| Privacy | Exposes all visited domains. | Hides domain lookups from third parties. |
Ultimately, DoH takes a vulnerable, public process and secures it within the modern, encrypted web standard we already trust for everything else.
How DoH Protects Your Web Browsing Journey
Let's break down what actually happens when you click a link or type a website into your browser. It seems instant, but a flurry of activity happens behind the scenes. DNS over HTTPS (DoH) steps into this process and adds a critical layer of privacy, shielding your activity from prying eyes.
Think of traditional DNS like sending a postcard. Anyone who handles it along the way—your internet provider, a network admin at your office, or a hacker on public Wi-Fi—can easily read the address you're trying to reach, like "mybank.com." There are no secrets.
DoH takes that postcard and seals it inside a locked, opaque envelope. It packages your request securely, so no one can peek at the contents while it's in transit.
Step 1: The Secure Handshake
When you hit Enter, your browser still needs to ask the same basic question: "What's the IP address for this website?" But instead of shouting that question across an open room, DoH does something much smarter.
It wraps the DNS query inside a standard HTTPS request—the very same secure protocol that protects your credit card details when you shop online. This new, encrypted package is then sent to a special DoH-compatible DNS resolver.
Since the request travels over port 443, the standard port for all secure web traffic, it blends in perfectly with everything else your device is doing online. It’s like hiding a specific conversation in the middle of a bustling, noisy crowd.
With DoH, your DNS request is no longer a distinct, easily identifiable piece of data. It blends seamlessly into the encrypted web traffic that constantly flows from your device, making it incredibly difficult for third parties to isolate and inspect.
This simple act of camouflage is the secret to DoH's power. It takes a historically vulnerable part of web browsing and wraps it in the gold standard of modern web security.
Step 2: The Encrypted Journey and Private Response
Once the DoH resolver gets the HTTPS package, it securely unwraps it, finds the IP address you asked for, and prepares the reply. But the security doesn't stop there.
The resolver takes the answer—the IP address—and places it back into a new, encrypted HTTPS response. This secure package travels directly back to your browser, and only your browser has the key to open it.
Here’s why that matters:
- No Eavesdropping: From start to finish, the entire conversation is private. No one in the middle can see where you're going online.
- Data Integrity: The encryption also guarantees the response you get is authentic and hasn't been maliciously changed to send you to a fake website.
This diagram shows the difference between the open, vulnerable path of a standard DNS request and the secure, private journey that DoH provides.
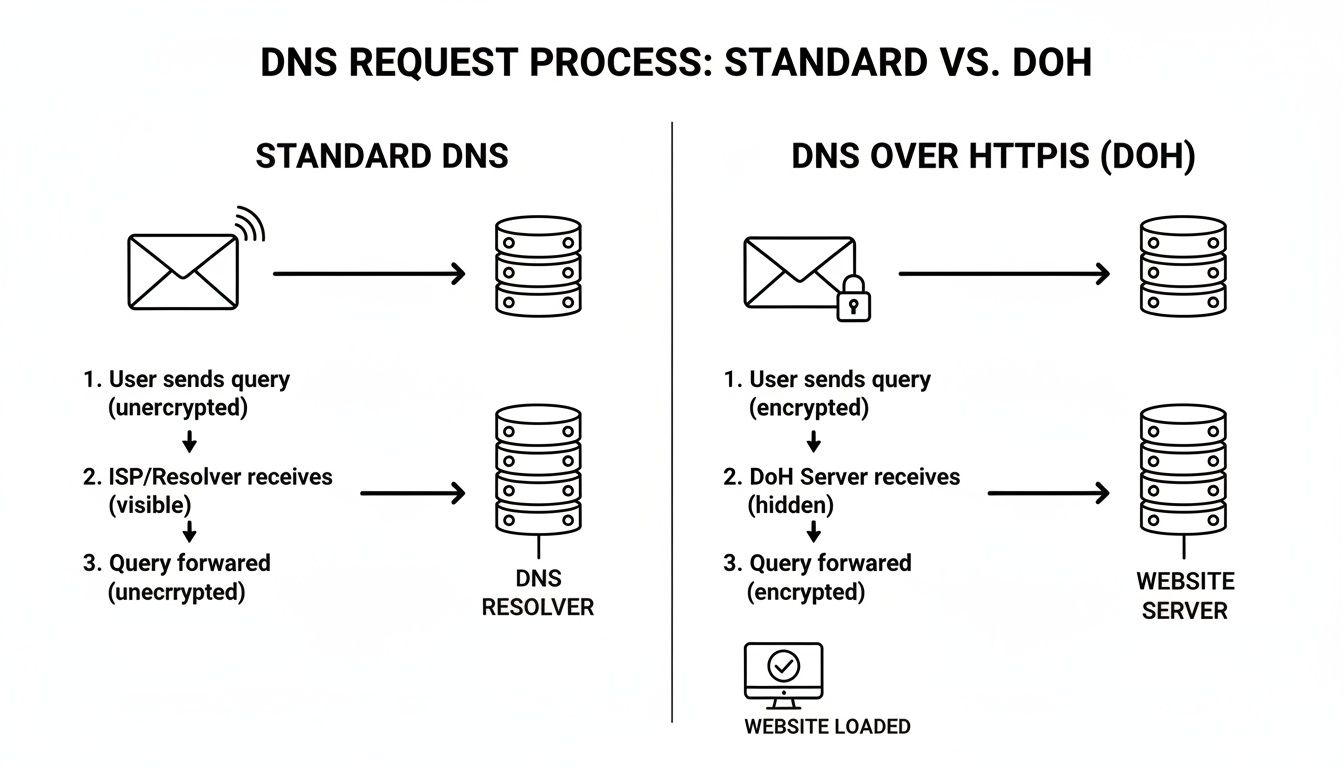
As you can see, the "sealed envelope" approach of DoH is a complete game-changer for privacy.
Finally, your browser receives the encrypted response, opens it, and connects you to the website. The page loads just as quickly as ever, but your digital footprint was protected the entire time. This layer of security works great alongside other privacy tools. To learn more, check out our guide on how a cookie manager can give you even more control. This end-to-end encryption is what makes DoH such a big step forward for a more private internet.
What Are the Real-World Benefits of Using DoH?
Switching to DNS over HTTPS (DoH) is about more than just a minor privacy tweak. It gives you real, practical control over your digital footprint, securing your online activity in ways the old-school DNS system was never designed to handle.
The most obvious win? It stops your Internet Service Provider (ISP) from keeping a running log of every site you visit. Standard DNS queries are sent in plain text, making your browsing history an open book. DoH encrypts those lookups, effectively slamming that book shut.
Think of it as a private tunnel for your DNS requests. Only you and the DNS resolver on the other end know where you’re trying to go.
Finally, Safe Public Wi-Fi
We’ve all been there—connecting to the free Wi-Fi at a coffee shop, airport, or hotel. But these networks are a playground for attackers, who can easily eavesdrop on unencrypted traffic. A common tactic is the man-in-the-middle (MITM) attack.
Here’s how it works: you try to go to your bank's website. An attacker on the same network intercepts your unencrypted DNS request and feeds you a fake IP address, sending you to a convincing-but-malicious copy of the site. With DoH, this entire attack falls apart. Your DNS query is encrypted and unreadable to them, ensuring you always land on the real website.
By encrypting DNS traffic, DoH hardens your defenses against common threats like DNS spoofing and hijacking, making public Wi-Fi significantly safer to use.
It's a simple, powerful defense against a very real threat that targets people on insecure connections every day.
Getting Around Web Censorship and Filters
DoH is also a powerful tool for keeping the internet open. Many companies, schools, and even entire countries block access to content by filtering DNS requests. When you try to visit a restricted site, their DNS server simply won't give you the correct IP address.
Because DoH sends your queries directly to a resolver you trust, it sails right past most local DNS filters. This means you can get to content that might otherwise be blocked.
Here’s where it really makes a difference:
- Bypassing ISP-level blocks: Some providers filter certain websites for commercial or policy reasons. DoH gets you around that.
- Overcoming network restrictions: If your work or school network blocks sites you need for research or news, DoH can often restore access.
- Promoting a free flow of information: In places with heavy internet censorship, DoH can be an essential tool for reaching the global, unfiltered web.
This shift empowers you to decide what you can see online, rather than leaving that control to the network you happen to be on. According to security provider Quad9, this is part of a larger trend. They predict that by 2025, privacy-first DNS services will be a standard defense against threats like phishing that exploit weak, unencrypted DNS. You can explore why privacy-centric DNS is critical to see just how important this technology is becoming.
Comparing DoH vs DoT vs Traditional DNS
While DNS over HTTPS (DoH) gets a lot of attention for boosting online privacy, it's not the only game in town when it comes to encrypted DNS. To really get why DoH is unique, we need to put it side-by-side with its older sibling, DNS over TLS (DoT), and the classic, unencrypted DNS that the internet was built on.
Each protocol handles security and privacy differently, which leads to some important trade-offs. The right choice often boils down to balancing the need for strong encryption against network management and how easily the protocol can be deployed.
Let's dive into what sets them apart and explore why browsers and modern operating systems are increasingly leaning toward DoH.
DNS Over TLS A Direct Approach to Encryption
Before DoH became the new standard, DNS over TLS was the go-to for locking down DNS lookups. DoT works by wrapping your DNS queries in a secure Transport Layer Security (TLS) tunnel—the same powerful encryption that secures HTTPS websites.
The key difference is that DoT operates on a dedicated port: port 853. This direct-line approach is efficient and creates a secure channel just for DNS. It basically announces to the network, "Hey, I'm an encrypted DNS query!"
While that's great for security, it’s also its Achilles' heel. Because it uses a unique port, network administrators can easily spot and block traffic on port 853 to enforce local DNS filtering rules. This makes DoT a fantastic choice if you just want encryption and don't mind that your DNS traffic is identifiable.
The Stealth Advantage of DNS Over HTTPS
This is where DoH pulls away from the pack. Instead of a dedicated port, DoH cleverly masks DNS queries by sending them over port 443—the same port used for all standard, secure HTTPS web traffic.
That one small change has a huge impact.
Because DoH traffic looks exactly like the encrypted data from countless other websites and apps, it’s nearly impossible for a network observer to pick out and block just your DNS requests without causing major disruptions to all web browsing.
This "camouflage" is DoH’s secret weapon. It delivers not only encryption but also a level of stealth that DoT just can't match. This makes it an incredibly effective tool for getting around DNS-based censorship and overly restrictive network policies. It's the main reason browsers like Chrome and Firefox have baked it in as their preferred secure DNS method. Privacy-first tools like the ShiftShift Extensions Domain Checker also rely on DoH to keep your domain lookups completely private and out of sight.
A Head-to-Head Comparison
To lay it all out, let's look at an in-depth comparison. This table highlights the practical differences between the old-school protocol, its first encrypted successor, and the modern, stealthy standard.
Detailed Feature Comparison of DNS Protocols
An in-depth look at the technical and practical differences between the three main DNS protocols.
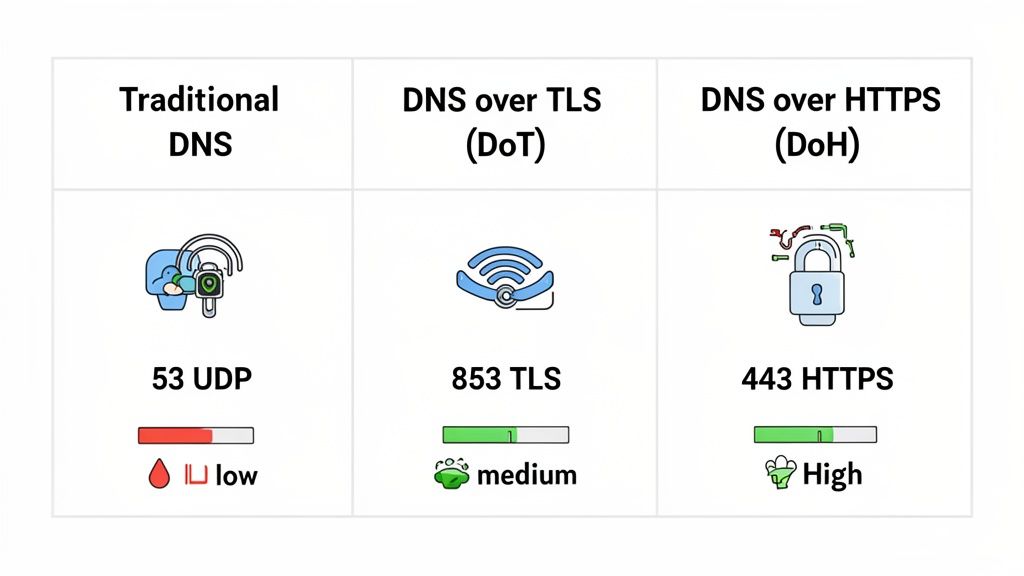
| Attribute | Traditional DNS | DNS over TLS (DoT) | DNS over HTTPS (DoH) |
|---|---|---|---|
| Encryption | None (Plain Text) | Full TLS Encryption | Full HTTPS Encryption |
| Port Used | Port 53 | Port 853 | Port 443 |
| Visibility | Completely exposed and easy to monitor | Encrypted, but easily identifiable as DNS traffic | Encrypted and blends in with regular web traffic |
| Privacy | Exposes every domain lookup | Protects against content inspection | Protects content and camouflages the request itself |
| Blockability | Easy to block or redirect | Relatively easy to block by port | Very difficult to block without broad disruption |
| Primary Use | Legacy internet infrastructure | Securing DNS on trusted networks | Enhancing user privacy and bypassing censorship |
In the end, both DoH and DoT are a massive security upgrade from traditional DNS. DoT offers a straightforward, dedicated channel for securing your lookups. However, DoH’s clever ability to blend in with everyday web traffic gives it a powerful advantage, especially on networks with heavy monitoring or filtering, making it the clear favorite for privacy-focused tools and users today.
Understanding the Criticisms and Trade-Offs
While DNS over HTTPS (DoH) is a huge win for individual privacy, it's not a silver bullet. Like any new technology, it comes with its own set of challenges and trade-offs. It's crucial to look at the whole picture and understand the legitimate concerns that have come with DoH's growing popularity.
One of the biggest arguments against it is the risk of DNS centralization. Most web browsers, by default, funnel DoH requests to a small circle of massive providers like Google, Cloudflare, and Quad9. Even though these companies have strong privacy policies, this setup effectively puts the internet's address book in the hands of a few corporate giants.
This just swaps one problem for another. Instead of your local Internet Service Provider (ISP) having a window into your browsing habits, that visibility now shifts to a different tech behemoth. For anyone uneasy about corporate data tracking, that's a significant concern.
The Network Management Dilemma
For the folks managing networks—whether in a company, a school, or even a home with parental controls—DoH can be a massive headache. They have long relied on monitoring DNS traffic to keep their networks safe and sound.
This kind of oversight is essential for:
- Enforcing Security Policies: Blocking traffic to domains known for malware, phishing scams, and botnet command centers.
- Content Filtering: Keeping inappropriate or adult content off the network in places like schools and homes.
- Regulatory Compliance: Making sure network activity meets specific legal or industry requirements.
DoH essentially blows past all these traditional, DNS-based safeguards. Because the DNS queries are encrypted and look just like normal HTTPS web traffic, they become completely invisible to most firewalls and filtering appliances. This can weaken a network's defenses and punch holes in carefully crafted security policies.
The core conflict here is a classic tug-of-war: individual user privacy versus centralized network control. The very feature that empowers a user to sidestep censorship also allows an employee to bypass critical security filters.
This has sparked a heated debate in the industry. Security professionals point out that DoH, despite its good intentions, can blind the very tools designed to protect us. We've even seen malware start using DoH to disguise its communications, making it much harder to spot and shut down.
Finding a Balanced Approach
This whole debate really just shows that DoH isn't a one-size-fits-all solution. For an individual using a sketchy public Wi-Fi network at a coffee shop, its benefits are crystal clear. The risk of someone snooping on your activity is high, and DoH adds a vital layer of protection.
But in a managed environment like a corporate office or a school, the calculation is different. Here, the need for network-wide security and content filtering often takes priority over the privacy boost from encrypted DNS. This is exactly why many organizations choose to block DoH on their networks, forcing all DNS requests back through their own monitored servers.
In the end, truly understanding what DNS over HTTPS is means seeing both its power and its pitfalls. It’s a fantastic tool for bolstering personal privacy, but how and where it's used requires some careful thought. For network admins, adapting to a world with DoH means evolving their security strategies and finding new ways to protect their users without relying on old-school DNS monitoring.
How to Enable and Test DNS Over HTTPS
Flipping the switch to DNS over HTTPS is a lot easier than you might think. Most of the web browsers and operating systems we use every day already have DoH support built right in, meaning you can add a serious layer of privacy to your browsing with just a few clicks.
This guide will walk you through turning on DoH on the most common platforms. After you get it set up, we'll cover how to quickly check that your DNS traffic is actually being encrypted and kept out of sight.
Activating DoH in Your Web Browser
For most of us, the simplest way to get started with DoH is to enable it directly inside the web browser. This approach is great because it encrypts all the domain lookups your browser makes, no matter what your computer’s main network settings are.
Google Chrome
- Click the three-dot menu icon up in the top-right corner and head to Settings.
- From there, go to Privacy and security, and then click on Security.
- Scroll down to the "Advanced" area and look for the Use secure DNS option.
- Toggle it on. By default, Chrome tries to use your current internet provider's service if it supports DoH. For better privacy, I'd recommend selecting "With" and choosing a specific provider like Cloudflare (1.1.1.1) or Google (Public DNS).
Mozilla Firefox
- Click the three-line "hamburger" menu in the top-right corner and choose Settings.
- Stay in the General panel, scroll way down to Network Settings, and click the Settings... button.
- In the new window that pops up, scroll to the bottom and check the box for Enable DNS over HTTPS.
- You can then pick a provider from the list or enter a custom one if you have a favorite.
Enabling DoH in your browser is a quick win for privacy. It secures the vast majority of your web activity without requiring deep technical changes to your operating system.
Enabling DoH on Your Operating System
If you want protection that goes beyond just your web browser and covers other apps, you can enable DoH at the operating system level. It's important to know that while this is a standard feature on Windows 11, it never officially made it to Windows 10.
Windows 11
- Open up Settings and go into Network & internet.
- Choose the connection you're using, either Wi-Fi or Ethernet.
- Click on Hardware properties.
- Look for DNS server assignment and click the Edit button next to it.
- Switch the setting from "Automatic (DHCP)" to Manual.
- Turn on IPv4 and type in the IP addresses for your DoH provider (for Cloudflare, that’s
1.1.1.1and1.0.0.1). - Now, in the Preferred DNS encryption dropdown menu, select Encrypted only (DNS over HTTPS). Hit Save, and you're done.
How to Confirm DoH Is Working
Once you've enabled DoH, it’s a good idea to make sure it’s actually running. A quick check will give you peace of mind that your DNS requests are properly encrypted.
A great tool for this is Cloudflare's Browsing Experience Security Check. Just load the page, and it automatically runs a few tests on your connection. The one you care about is "Secure DNS"—a green checkmark means your queries are being sent over an encrypted channel.
If you get the green light, you're all set. If not, go back and double-check your settings or maybe try a different DoH provider. Keep in mind that a sluggish connection can sometimes interfere with test results; you can learn more about how to test internet speed accurately in our dedicated guide.
Frequently Asked Questions About DNS Over HTTPS
As more people start using DNS over HTTPS, a few common questions always seem to pop up. Getting to the bottom of these helps you understand where DoH really fits in your privacy toolkit and what to expect when you flip the switch. Let's dig into the most frequent ones.
Will Using DoH Slow Down My Internet Connection?
For the most part, no. The impact DoH has on your browsing speed is usually so small you'll never notice it. While adding encryption does technically introduce a tiny bit of overhead to each DNS request, modern computers and networks are so fast they handle it without breaking a sweat.
In some cases, you might even see a speed boost. If your internet provider's default DNS servers are sluggish, switching to a high-performance DoH service from a provider like Cloudflare or Google can actually make websites load faster. Any minuscule latency from the encryption is a tiny price to pay for the huge privacy and security upgrade.
The bottom line: for most people, the performance difference is negligible. The security you gain from encrypted DNS is well worth it.
Is DoH a Complete Replacement for a VPN?
Not at all. Think of DoH and a Virtual Private Network (VPN) as two different tools that work brilliantly together. እነሱ የመስመር ላይ የግለሰቦች ጥበቃ ፈተና ውስጥ በአንደኛ ደረጃ ነገር ይለያዩ፣ ነገር ግን በአንደኛ ደረጃ እንደ አስፈላጊ ነገር ይቆጠራሉ።
እነሱን የሥራ አይነቶች በቀላሉ ለማየት እነዚህ ናቸው:
- DNS በ HTTPS (DoH): ይህ የ DNS ምርመራን በተለይ ይይዛል - የእርስዎ አውታር ወደ ድህረ ገፅ የ IP አድራሻ ሲጠይቅ ይሆናል። ይህ የግለሰቦች የሚያዩትን ድህረ ገፆች ማየት ይከለክላል።
- ቪርቹዋል የግል ኔትወርክ (VPN): ይህ የእርስዎን የአይነት ተመን ይይዛል ሁሉም የአይነት እንቅስቃሴ እና ወደ ድህረ ገፆች የሚገኙትን የእውነተኛ የ IP አድራሻዎትን ይደብቃል። ይህ የእርስዎን የመስመር ላይ የሚያደርጉትን ሁሉ እንደ አጠቃላይ የግለሰቦች ጥበቃ ይሆናል።
አንድ ምሳሌ ይረዳል፡ DoH ወደ መድረክ አድራሻዎትን በተዘጋጅቷ የግለሰቦች አድራሻ ውስጥ ይገኛል። አንድ VPN ግን ወደ ዚያ ለመድረስ የሙሉ መኪናዎትን በታላቅ የተደበደበ ታክስ ውስጥ ይገኛል። ለበለጠ ጥበቃ ሁለቱንም መጠቀም ይፈልጋሉ።
እኔ ከ DoH ጋር የምጠቀም እንደ ሥራ ተቋም መረጃ ማየት ይቻላል?
DoH ቢኖርም በአንደኛ ደረጃ በኩባንያ ወይም በትምህርት ኔትወርክ ውስጥ እንደ እርስዎ የማይታይ አስበው አይደለም። ይህ የተለመዱ የማይታይ አስበው ይሆናል፣ ነገር ግን ይህ የተለየ የኔትወርክ እንቅስቃሴ እንደ ወይን ይሆናል።
እንደ እኔ የሚያዩት የሚሆን አንድ የኔትወርክ አስተዳደር የእርስዎን እንቅስቃሴ ይገኛል። የ DNS ምርመራዎች ቢወድቁም የአይነት አድራሻዎትን ይመለከታል። በጣም አስፈላጊ ነገር የሚሆን የሥራ የተሰጠ መሳሪያዎች በቀጥታ የሚያዩት የሚሆን የእኔትወርክ የሚሆን የሚያዩት ይገኛል። DoH የግለሰቦች ጥበቃ ለመሆን ይህ የተሻለ ደረጃ ነው፣ ነገር ግን የኩባንያው የሚሆን የሚያዩት የሚሆን የሚያዩት ይገኛል።
የእርስዎን የመስመር ላይ የሚያዩትን ይህ ይዘው ወይም የሥራዎትን ይቀርቡ? ShiftShift Extensions ኢኮስተም በድህረ ገፅዎ ውስጥ የተያያዘ የኃይል መሳሪያዎች ይይዛል፣ የሚያይዝ የ Domain Checker ይይዛል ወደ ድህረ ገፆች የ DNS-over-HTTPS ይጠቀማል። የዲጂታል ዕድልዎን በአንድ የተወካዩ የኮማንድ ፓሌት በ ShiftShift Extensions ይዘው ይወድቁ።