How to Create Secure Passwords That Actually Work
Learn how to create secure passwords with our guide. We cover strong passphrases, essential password managers, and why you need two-factor authentication.

የተመነጨ ማስተካከያዎች
To really lock down your accounts, you need passwords that are long, complex, and—most importantly—unique for every single site you use. The best way to do this is either by creating a passphrase (a memorable string of four or more random words) or by letting a password manager generate and store impossibly random character strings for you.
Why Your Old Password Habits No Longer Work

Let's be honest, the old advice—"just add a number and a symbol to a common word"—is completely outdated. The digital world has evolved, and so have the threats. A password like Password!1 might check a box on a registration form, but it’s an open door for modern cyberattacks.
Hackers aren't manually guessing passwords anymore. They use automated tools that can cycle through billions of combinations a second. This is called a brute-force attack, and it makes short, predictable passwords laughably easy to crack. Even clever substitutions like 'Pa$$w0rd' won't fool these programs for long, as they're specifically designed to check for those common tricks.
The Domino Effect of Just One Weak Password
Here’s where it gets really scary. A single weak password can act like a master key to your entire digital life, setting off a catastrophic domino effect. This happens all the time because of a common attack called credential stuffing.
Cybercriminals get their hands on a list of usernames and passwords from a data breach at one company. Then, they use bots to automatically try those same login details on hundreds of other popular sites—your bank, your social media, your email.
This works so well because most people reuse passwords everywhere. Despite years of warnings, an astonishing 80–85% of people still reuse the same password across multiple websites. You can dig into the data on this password crisis, but the takeaway is clear: this habit creates a massive, self-inflicted vulnerability.
"Your passwords are your 'first factor,' i.e. 'something you know.' The goal is to make that 'something' so difficult for an attacker to guess or discover that they simply move on to an easier target."
To help you get started, here's a quick cheat sheet covering the core principles we'll be discussing.
Quick Guide to Secure Passwords
| Principle | Why It Matters | Quick Tip |
|---|---|---|
| Length is Key | Longer passwords are exponentially harder for bots to crack. | Aim for at least 16 characters or 4 random words for a passphrase. |
| Embrace Randomness | Predictable patterns, dictionary words, and personal info are easy guesses. | Use a mix of upper/lowercase letters, numbers, and symbols. A password generator is your best friend here. |
| One-of-a-Kind | If one account is breached, password reuse lets attackers into your other accounts. | Every single account needs its own unique password. No exceptions. |
| Use a Password Manager | It's impossible to remember dozens of unique, complex passwords. | Let a password manager generate, store, and autofill them for you. |
| Enable 2FA | Adds a critical second layer of defense, stopping anyone who manages to steal your password. | Turn on two-factor authentication on every account that offers it. |
Think of this table as your foundation. Now, let's build on it.
Adopting a Modern Security Mindset
Protecting yourself means you have to change your strategy. Forget trying to memorize dozens of slightly different, complex passwords. It’s time to adopt a modern approach built on three core pillars:
- Build Strong Passphrases: Instead of struggling with things like
R#8b^t!P9, switch to long, memorable passphrases. A phrase like "BrightPurpleRobotDancesWeekly" is far stronger and a whole lot easier to recall. - Use a Digital Vault: A password manager is non-negotiable in today's world. It acts as a secure vault for all your unique passwords and can generate new, unbreakable ones whenever you need them. The burden of memorization is just... gone.
- Activate Your Ultimate Defense: Think of two-factor authentication (2FA) as your digital deadbolt. It requires a second piece of proof—usually a code from your phone—making your password useless to a thief without it.
By mastering these three concepts, you shift from being a potential victim to a well-defended user. In this guide, I'll walk you through exactly how to put each one into practice.
Crafting Unforgettable and Unbreakable Passphrases
If you’ve ever wanted to throw your keyboard across the room trying to remember something like !Tr0ub4dor&3, I get it. We've all been there. But here's the secret: a truly strong password isn't about being impossible to remember—it's about being impossible for a computer to guess. This is where the simple brilliance of the passphrase comes in.
A passphrase is just a string of words that you can easily bring to mind, but for a machine, it’s a mathematical nightmare. The concept is based on the 'diceware' method, which is a fancy way of saying "string together random words." The more words you add, the exponentially harder it gets for brute-force attacks to crack.
Think about it this way: modern cracking tools can churn through billions of combinations a second. An eight-character password, even with symbols, can be busted in minutes. But a simple four-word passphrase? Something like the classic CorrectHorseBatteryStaple would take today's tech thousands of years to figure out.
The Formula for a Flawless Passphrase
The magic ingredient here is randomness. Your goal is to string together words that have absolutely no logical connection. This is non-negotiable, because attackers use massive dictionaries and "rainbow tables" filled with common phrases, song lyrics, and famous quotes. A line from your favorite movie is a terrible idea.
To get started, think of it like a security-focused game of Mad Libs.
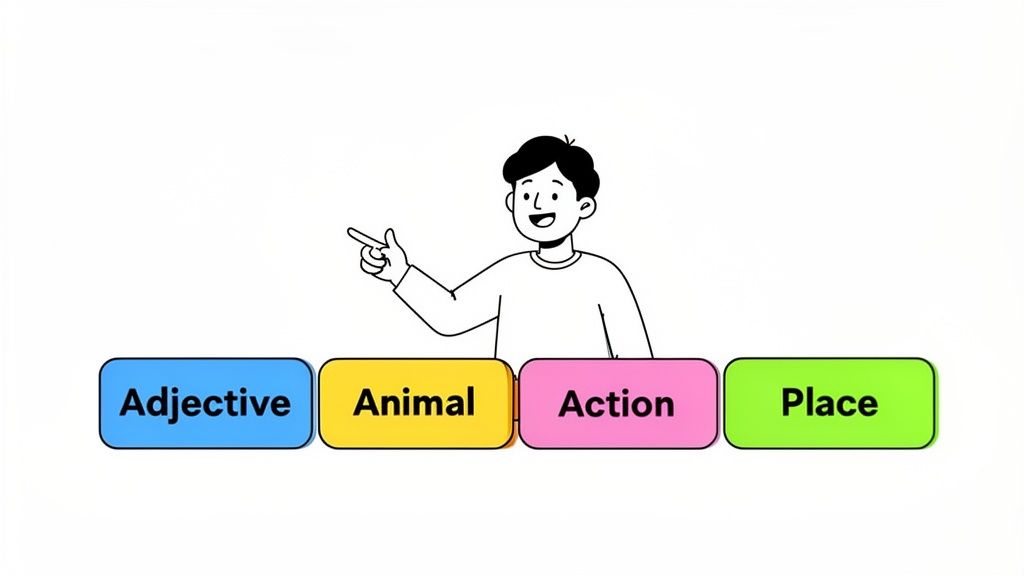
- A Simple Formula:
[Adjective][Animal][Action][Place]
Using a structure like this, you can generate phrases that are both highly memorable and totally random. You might end up with "SleepyGiraffeJugglesParis" or "AnxiousBadgerDrivesMars." The bizarre mental images these create actually make them stick in your head far better than a jumble of symbols.
The real strength of a passphrase lies in its entropy—a measure of its unpredictability. A chain of four unrelated words creates vastly more entropy than a single complex dictionary word with a few numbers tacked onto the end.
Common Passphrase Pitfalls to Avoid
Even with a great method, it's surprisingly easy to fall into traps that weaken your passphrase. When you're building your own, make sure you steer clear of these common mistakes:
- Predictable Sequences: Avoid phrases built from personal info or common expressions, like "I love my dog spot" or "GoPackGoChamps2024." They're the first things an attacker will try.
- Pop Culture References: Lyrics, movie quotes, and book titles are all over the internet—and in every hacker's dictionary. A phrase like "LukeIAmYourFather" is just as bad as "password."
- Adjacent Keyboard Patterns: We all know "qwerty" is a weak password. The same logic applies to phrases like "TheQuickBrownFox." It's too well-known.
The aim is to create something that feels unique to you without being personally identifiable. The more nonsensical the combination, the better your defense.
Adapting a Base Passphrase for Different Accounts
Look, you absolutely need a unique password for every single site. But you don't have to start from scratch every time. A smart technique is to create one strong "base" passphrase and then add a unique, site-specific modifier to it. This gives you a solid manual system for your most important accounts.
Let's say your base passphrase is AnxiousBadgerDrivesMars. You could adapt it for different sites like this:
| Account Type | Site | Modifier Logic | Final Passphrase Example |
|---|---|---|---|
| G-Mail | Add a symbol + the first/last letters of the site. | AnxiousBadgerDrivesMars@gl |
|
| Banking | Ch-ase | Use a different symbol + the first two/last two letters. | AnxiousBadgerDrivesMars#chse |
| Social | Tw-itter | Use another symbol + a different letter combo. | AnxiousBadgerDrivesMars%twr |
This simple system gives you a repeatable pattern that you can remember, but it still generates a distinct credential for each account. It’s a practical balance between iron-clad security and the reality of human memory, making it a great strategy for anyone just learning how to create secure passwords.
Let a Password Manager Do the Heavy Lifting
Coming up with strong passphrases is great for your most important accounts—your email, your banking—but let's be realistic. Most of us have dozens, if not hundreds, of online logins. Trying to create and remember a unique, high-entropy passphrase for every single forum, streaming service, and online store is a recipe for failure. It's just not practical.
This is where a password manager becomes your best friend. Seriously, it's the single most important security tool you can adopt. Think of it as a fundamental shift in how you handle your digital life. Instead of juggling a mess of weak, recycled passwords, you only need to remember one thing: your master password.
The manager does all the hard work from there. It acts like a digital vault, securely generating, storing, and even autofilling incredibly complex passwords for every site you use. Right away, this solves the two cardinal sins of password security: reuse and weakness.
Why a Password Manager Is Non-Negotiable
A good password manager takes human error out of the equation. It automates all the best practices and removes the temptation to just use Password123! again because it's easy. You're not just storing passwords; you're fundamentally upgrading your security posture.
Here’s what you get right out of the box:
- Effortless Uniqueness: The manager can instantly create a random, gibberish password like
k9#Z&p8!vR@qG$fTfor that new account you're signing up for. You never even have to see it, let alone try to remember it. - Secure Storage: Your password vault is locked down with powerful encryption. This means even if the password manager company itself was breached, your data would be useless to hackers without your unique master password.
- One-Click Logins: Modern managers plug right into your browser, filling in your login details for you. This is a huge timesaver, but it's also a great security feature—it protects you from phishing sites because the autofill simply won't work on a fake or lookalike domain.
The whole idea is to outsource the impossible task of remembering hundreds of unique, random passwords to a tool built specifically for that job. This frees you up to focus on protecting the one password that actually matters—the key to your entire vault.
If you're not quite ready to jump into a full-fledged manager, some lightweight browser tools can bridge the gap. For instance, the Password Generator within the ShiftShift Extensions suite gives you a quick and easy way to create a strong password on the fly.
Tools like this offer immediate access to secure password generation without the commitment of a separate app, making it that much easier to secure new accounts the moment you create them.
Choosing the Right Password Manager
When you’re ready to commit, remember that you’re entrusting this service with the keys to your entire digital life. It's a big decision, so choosing wisely is critical.
Here are the non-negotiable features you should look for:
- Zero-Knowledge Encryption: This is the gold standard. It means the company providing the service has zero ability to access or decrypt your data. Only you, with your master password, can unlock the vault.
- Third-Party Security Audits: Reputable services hire independent cybersecurity firms to hammer on their systems and find any weaknesses. Look for companies that are transparent about these audits.
- Cross-Platform Syncing: A password manager is only useful if it's everywhere you are. Make sure it works seamlessly on your computer, phone, and tablet.
- Robust 2FA Options: The manager itself needs to be locked down tight. It should support two-factor authentication, ideally with options for authenticator apps or even physical security keys.
As you start looking, it helps to see how the top contenders measure up. For example, you can compare leading password managers like 1Password and LastPass to dig into the specifics of their security models, features, and overall user experience.
Your Most Important Password Ever
Once you’ve picked your manager, it’s time to create your master password. This is it—the one password you absolutely, positively have to remember. It needs to be a fortress.
This is the perfect time to use the passphrase method we talked about earlier. A great master password should be:
- Long: Go for at least six to eight random, unconnected words.
- Memorable (to you): Create a bizarre or funny phrase that will stick in your head but mean nothing to anyone else.
- Totally Unique: This password cannot have been used anywhere else. Ever.
A solid master password could be something like OrangeSpaceshipQuietlyPaintsAzureMountains. It's incredibly difficult for a computer to crack but simple enough for you to recall. While you're memorizing it, write it down and store it somewhere physically secure, like a safe deposit box or a fireproof safe at home. This single password is the bedrock of your entire digital security strategy.
Your Digital Deadbolt: Adding a Layer of Security with 2FA
Let’s be honest: even the most brilliant passphrase or randomly generated password can be stolen. A clever phishing email, a massive data breach at a company you use, or even spyware on your own computer can expose your login credentials. That’s why a strong password is only half the battle.
The other half is adding a digital deadbolt: Two-Factor Authentication (2FA).
Think of it like this. Your password is the key to your front door. If a thief gets a copy, they can just walk right in. 2FA is that extra deadbolt on the inside—a completely separate lock that needs a different kind of key. It works by combining something you know (your password) with something you have (like your phone or a physical security key).
So, even if a hacker snags your password, they're stopped cold because they don't have that second piece of the puzzle. To really lock down your accounts, you need to go beyond just a good password. A great starting point is understanding two-factor authentication (2FA) and why it’s one of the most effective things you can do to protect your digital life.
The Different Flavors of 2FA
Not all 2FA methods offer the same level of protection. They range from "good enough" for some accounts to "fortress-level" security for your most critical ones. Knowing the difference helps you pick the right tool for the job.
Here’s a quick rundown, from least to most secure:
- SMS Text Messages: This is the one you’ve probably seen the most. You try to log in, and a service texts a one-time code to your phone. While it’s way better than nothing, this method is vulnerable to a scam called "SIM swapping," where a criminal tricks your phone company into moving your number to their device.
- Authenticator Apps: Apps like Google Authenticator or Authy generate a fresh, time-sensitive, six-digit code every 30 seconds. This is a huge leap in security from SMS because the code is created right on your device and never travels over the vulnerable cellular network.
- Physical Security Keys: This is the gold standard. A physical key, like a YubiKey, is a small USB device you plug into your computer or tap on your phone to approve a login. It's almost completely immune to phishing and remote attacks, offering the strongest security available to the average person today.
For your really important stuff—email, banking, password manager—I strongly recommend using an authenticator app or, even better, a physical key.
How to Get 2FA Set Up
Flipping the switch on 2FA is usually pretty painless and can be found in the "Security" or "Account" settings of most major websites and apps.
The first step almost always involves scanning a QR code with your authenticator app to link the account. That quick scan is what creates the secure connection for generating all your future codes. If you're curious about how that works, our guide explains how to generate a QR code and what’s inside it.
Let's walk through the typical steps you'd take to enable it on your main email account:
- Head to Security Settings: Log in to your account and dig around for the security or login settings page.
- Look for the 2FA Option: You’ll see it called different things, like "Two-Factor Authentication," "2-Step Verification," or "Login Approvals."
- Pick Your Method: The site will ask how you want to get your codes. If you see an "Authenticator App" option, always choose it over SMS.
- Link Your App: A QR code will pop up on your screen. Just open your authenticator app on your phone, tap the "+" button, and scan the code. This adds the account to your app's list.
- Verify and Save: Type in the six-digit code from your app to prove you linked it correctly. The next screen is critical—the service will show you a list of backup codes.
Pro Tip: Don't just click past the backup codes. Save them immediately. Print them out or write them down and stash them somewhere safe, like in a fireproof box or a locked drawer. If you ever lose your phone, these codes are your only way back in.
Activating 2FA is a one-time setup that pays off every single day. Sure, it might add an extra five seconds to your login, but it builds a massive wall that keeps criminals out, even if they have your password. It's a tiny bit of friction for a huge gain in security.
How to Conduct a Personal Security Audit
Creating strong passwords and enabling 2FA for new accounts is a fantastic habit. But what about the digital trail you've already left behind? It's time to tackle the dozens—maybe even hundreds—of accounts you've created over the years. Think of it less as a chore and more as a digital deep clean.
The best place to start is by facing the music. You need to know where your information has already been exposed.
A tool I always recommend is Have I Been Pwned. Just pop in your email addresses, and it will show you every known data breach they’ve been a part of. It might be a bit of a wake-up call, but it gives you a concrete, prioritized list of accounts that need your immediate attention.
Prioritize and Conquer Your Accounts
Seeing that breach report can feel overwhelming. The key is not to try and fix everything at once—that’s a recipe for burnout. The smart approach is to categorize your accounts by risk and tackle them in waves.
Here’s a simple tier system I use:
- Tier 1 (High Priority): These are the crown jewels. If one of these is compromised, it could lead to identity theft or serious financial loss. We’re talking about your primary email, password manager, banking apps, and government service accounts. Start here, no exceptions.
- Tier 2 (Medium Priority): This group includes accounts holding a lot of personal data or payment info. Think major social media profiles (Facebook, Instagram), your go-to shopping sites like Amazon, and key work-related platforms.
- Tier 3 (Low Priority): These are the miscellaneous accounts—forums you signed up for once, old newsletters, or one-off services you've forgotten about. A breach here is less critical, but they still need to be cleaned up.
Work your way down from Tier 1. Honestly, just securing one high-priority account is a massive win for your overall security.
Your Security Audit Checklist
For every account you review, follow this straightforward process. It turns a vague goal into a clear set of actions, and you'll get faster with each one you complete.
- Check for Breaches: Confirm if the account's credentials have been exposed on Have I Been Pwned. If so, move it to the top of your list.
- Generate a New Password: Use your password manager to create a long, random, and completely unique password. This is a core part of learning how to create secure passwords that can stand up to today's threats.
- Enable 2FA: Dig into the account's security settings and switch on two-factor authentication. If you have the choice, always opt for an authenticator app or a physical key over SMS.
- Save Everything Securely: Store the new password, the 2FA backup codes, and any updated security questions right in your password manager.
Don't forget about the data stored right in your browser. Old cookies can sometimes hold onto session information, so it’s a good idea to clear them out after a major security overhaul. If you want to get more granular, you can learn how a cookie editor Chrome extension gives you more control.
This simple flowchart shows just how powerful 2FA is.
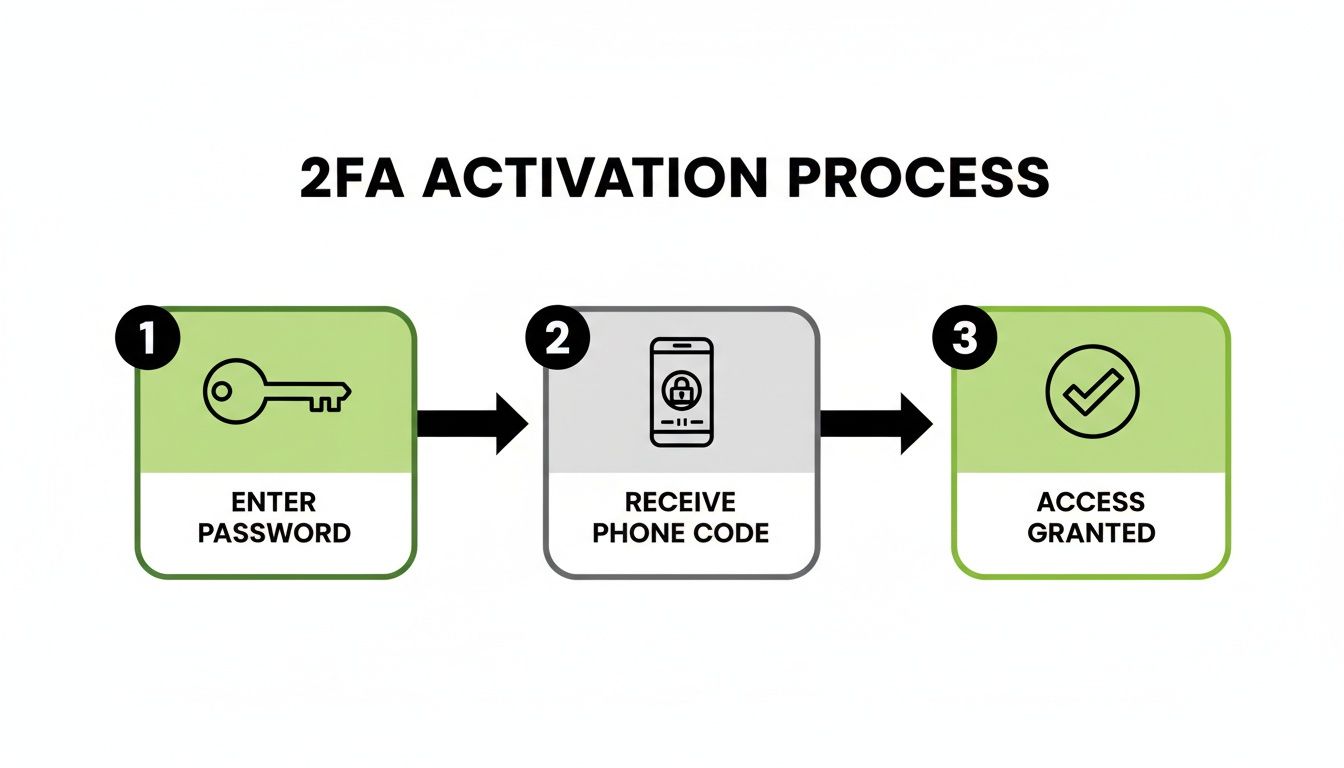
It perfectly illustrates that even if a thief gets your password (the key), they're stopped cold without the second factor from your phone.
Make Security an Ongoing Habit
A personal security audit isn't a one-and-done project; it’s a practice. I set a calendar reminder every six to twelve months to quickly review my most critical accounts. It’s a good time to check for new breaches and maybe rotate the passwords on my Tier 1 accounts.
When you treat your digital security as a continuous process, you build a much stronger defense. Every password you update and every 2FA toggle you switch on makes you a significantly harder target for attackers.
Putting It All Into Practice: Your Secure Password Playbook
Okay, let's move from theory to action. Getting your password security right isn’t about memorizing a bunch of complicated rules. It's about building a few smart habits and letting the right tools do the heavy lifting for you.
Think of it this way: your new playbook really just comes down to four key ideas.
First, strength comes from length and randomness. Whether you're creating a long, memorable passphrase for a critical account or letting a generator create total gibberish, entropy is what keeps you safe. A short, predictable password is like leaving your front door wide open for automated attacks.
Second, every single account gets its own unique password. I can't stress this enough. Reusing credentials is the fastest way to turn one small breach into a complete disaster, giving thieves the keys to your entire digital kingdom. This is the one rule you never, ever break.
Applying Your New Strategy in the Real World
So, what does this look like day-to-day? Well, you wouldn't use the same deadbolt for your bank vault that you use on your garden shed. The same logic applies to your online accounts.
High-Stakes Accounts (Banking, Email): These are the crown jewels. You need Fort Knox-level security here. Use a long, randomly generated password from a tool like the ShiftShift Extensions' Password Generator. Then, lock it down with the strongest two-factor authentication you can get—ideally, an authenticator app or a physical security key.
Low-Stakes Accounts (Forums, Newsletters): These still need unique passwords to stop credential stuffing attacks, but you can be more efficient. Just let your password manager generate and save a strong password with one click. The goal is security that doesn't slow you down.
The real goal here is to change how you think about passwords. Security isn't a chore; it becomes an almost automatic, empowering habit once you have a solid system in place. You're building a digital fortress, one secure login at a time.
This brings us to the last two pillars of your playbook: always use a password manager to store everything, and always turn on 2FA as your ultimate backup plan. The manager handles the impossible job of remembering dozens of complex passwords, and 2FA ensures that even if a password does get stolen, it’s completely useless to a thief.
When you bring these four elements together, you've got a simple, repeatable process for protecting yourself online. This isn't just another checklist; it's a fundamental shift that makes top-notch security feel effortless.
To keep building on this foundation, check out our deep-dive guide on the best practices for password security. With this playbook, you'll have the confidence and the tools you need to secure your corner of the digital world.
Got Questions About Password Security? We’ve Got Answers.
Even with the best plan in place, you're bound to have questions. Let's tackle some of the most common ones we hear, bust a few myths, and give you some practical advice to clear things up.
"Should I Be Changing My Passwords All the Time?"
This is a big one. For years, the standard advice was to change your passwords every 90 days. That thinking has completely changed.
If you’re already using strong, unique passwords for every single account—and you have them tucked away safely in a password manager—forcing yourself to change them on a schedule doesn't really add much security. In fact, it often does the opposite. People tend to make tiny, predictable tweaks, like changing Winter2023! to Spring2024!. Hackers know all about these patterns.
The modern, expert-backed advice is this: Set a strong, unique password and forget about it... until you have a good reason to believe it's been compromised. It's a far more effective and less frustrating way to stay secure.
"Is It Okay to Just Let My Browser Save My Passwords?"
Let's be clear: using your browser's built-in password saver is a whole lot better than using password123 everywhere. But it's far from the best option.
Think of it as a convenience feature, not a true security tool. Dedicated password managers are built with one purpose in mind: protecting your credentials with powerful, zero-knowledge encryption. Browser-based managers, on the other hand, are often tied directly to your browser profile, making them a juicy target for malware designed to steal that exact information. For real peace of mind, a standalone password manager is the way to go.
"What Do I Do If a Site I Use Gets Hacked?"
First, don't panic. Data breaches are unfortunately common, but if you've followed the advice in this guide, the cleanup is pretty straightforward.
Here’s your game plan:
- Change the Password Immediately. Head straight to the affected site and create a new, strong, unique password for it.
- Audit Your Accounts. If you (oops!) reused that password anywhere else, now's the time to change it on those other sites, too. A password manager makes finding these duplicates a breeze.
- Turn on 2FA. If you weren't already using two-factor authentication on that account, enable it right away. It's your best defense against someone using your stolen credentials.
When you have a solid system in place, a breach notification goes from a five-alarm fire to a minor, manageable task. You just update one entry in your vault and you’re done.
Ready to make all of this effortless? The ShiftShift Extensions suite comes with a built-in Password Generator and other essential security tools, all right there in a single command palette. Download it from the Chrome Web Store and take back control of your digital life.